The Art of Computer Virus Research and Defense Pdf Github
How To Respond Malware/Virus Spread?
Nosotros are living through historical moments of humankind considering of Coronavirus (COVID-19), which is pandemic now. My objective is to raise sensation of post-obit guidelines of health authorities and bespeak similarities about how do we respond virus spread in IT industry.
Computer viruses cause billions of dollars damage each twelvemonth due to causing system failure, corrupting information, increasing maintenance costs etc.
MyDoom was 1 of the nearly devastating and infectious computer virus, which caused over $38 billion in damages and 25% of all emails infected in 2004.
ILOVEYOU was another fatal and infectious computer virus that acquired over $10 billion amercement and spread 10% of the computer systems all over the earth. Half of those computer systems was infected within the first week in May 2000. It was then bad that governments and large corporations took their mailing system offline to prevent infection.
Stuxnet was the commencement cyberwarfare virus intended to disrupt nuclear efforts of Iran. It managed to ruin 1 5th of Iran'south nuclear centrifuges and that nearly 60% of infections were concentrated in Iran.

In this postal service, I will endeavour to highlight fundamentals computer malwares/viruses and how do nosotros respond them without boring you to death with technical details. I will effort to emphasize similarities of biological malwares/viruses such as Coronavirus (Covid-xix). I am not expert of the biological malwares/viruses so I will present my point of view as an IT professional.
What is Malware/Virus?
Malware is a malicious software intentionally designed to cause damage to a computer, server, client, or computer network. Therefore we can define Malware is the commonage name for variety of malicious software like computer viruses, worms, Trojan horses, ransomware, spyware, adware, and scareware.

A computer virus is a piece of code replicates itself by modifying other programs and spread from ane host to others when it is executed. Which often results damage to the host. A zero-day virus is a previously unknown estimator virus that has no known anti-virus signatures available.
A memory-resident virus (resident virus), installs itself equally part of the operating organisation when executed, and remains in RAM until information technology is shut down. Like some viruses stay permanently in the body. A non-memory-resident virus (non-resident virus), information technology does not remain in RAM after executed, scans for targets, infects them and then exits.
A biological virus is a microscopic infectious amanuensis that replicates within the living cells of an organism. Viruses tin can infect all types of life forms, people, animals, plants, microorganisms, including bacteria and archaea. A vaccine helps the torso's immune system to recognize and fight pathogens like viruses or bacteria, which then keeps us safe from the diseases they cause.

If we tin call signatures equally the vaccines of computer viruses. In that location is a similarity between COVID-19 and Zero-day virus. Considering there are no known drugs or vaccines for Coronavirus (COVID-nineteen).
What Are Signatures For Anti-virus Software?
A estimator virus signature is a unique pattern of code that is for detecting and identifying specific viruses. The antivirus software scans signatures and relies on signature database of known malicious codes. This is effective only cannot defend confronting zero-24-hour interval malware/virus, if no samples obtained signatures generated and updates distributed. Signature based method is vulnerable to obfuscation and diversity of other techniques. Therefore modern Anti-Virus software use more advanced methods (Heuristic: Similarity with related viruses, Real-time beliefs: Anomalies of the behavior, Sandbox and Signature).
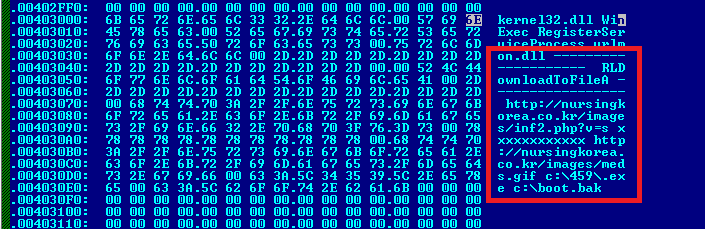
Signatures are outcome of the malware analysis performed past experts. Typically, at that place are 2 types:
- Static Malware analysis : Static or Code Analysis is a contrary applied science which is examining each component and relationships with other resources of the binary code without executing.
- Dynamic Malware analysis : Observing the beliefs of the malware while it is actually running on a sandboxed surround same as the host system.
Vaccines developed by taking viruses and weakening or killing them so that they cannot reproduce. The trunk'south allowed system recognize them as a threat and destroy it. Therefore, body'southward immune organization recognize and destroy whatever of the microorganisms associated with that virus it may run across in the futurity.
Similar to Anti-virus software companies who are developing signatures today many pharmaceutical companies working on developing a drug or vaccine for Coronavirus (COVID-19)
Components, Symptoms and Lifecycle of the viruses
Typically, a figurer virus has these iii components:
- Infection Vector : How the virus spread/propagate (Coronavirus through respiratory droplets, surface, close contact etc.)
- Trigger: Events/Conditions that will kickoff out the malicious function/payload (incubation of the coronavirus)
- Payload : Data/code performs the malicious actions (Coronavirus tin can lead to serious illnesses, like pneumonia or death)
There are 4 stages at the lifecycle of computer virus (As an analogy to biological science):
- Virus Entry (Dormant): The virus has managed to access the target host. (Coronavirus gets into body)
- Replication (Propagation): The virus starts propagating, that is multiplying and replicating itself. (Coronavirus starts infecting cells, replicating itself and propagates thru respiratory droplets)
- Triggering: The virus activated every bit a result of weather or the events, and so it starts performs the function that is intended. (the period between exposure to an infection and the appearance of the outset symptoms like incubation menses of coronavirus)
- Execution : The virus gets to work where payload is released, and the terminate user volition begin to observe problems such as deleted files, the system crashing or endless popups on the screen. (This is where infected person starts to encounter symptoms like cough, shortness of breath, fever and tin lead to serious illnesses, like pneumonia or death) (this is where body fights with the virus)
How Do Nosotros Respond (Information Security Incident Response)
Employee behavior can take big impact on information security in organizations. Like people beliefs can have big impact on virus spread in these days' pandemic. Therefore, employees are important function of information security chain in the organization. Like as people we are important part of the global effort in the security and health of loved ones and other people (especially elderly people).
In social club to reply incidents, there are two level of planning'southward:
- Strategic Plan: Executive level, Strategic Level
- Incident Response Plan: Operational Level, Tactical Level
Strategic Plan
Organization defines and communicate its executive-level strategy, priorities, management, performance and allocate its resources to achieve its strategic objectives and asses, adjust organization'southward management in response to irresolute environs on the whole business for data security.
Typically, at this level followings are done:
- Pre-Evaluation : to place employee sensation of information security and analyze electric current security policy.
- Strategic Planning: to come up up with a better sensation program, clear targets and grouping people or units to achieve goals.
- Operative Planning : Institute a good security practice based on internal communication, direction, awareness and a preparation program
- Implementation : Commitment of the direction, Commitment of employees, Communication and grooming for all members.
- Post-Evaluation : to appraise the success of the planning and implementation, and to identify areas of business concern.
This is similar to guidelines of WHO, CDC, ministry of wellness authorities. All over the world there are these sensation campaigns about importance of:
- STAY HOME, SOCIAL Altitude, PERSONAL AND FACILITY HYGIENE, DO Not STOCKPILE, ASSIST ELDERLY PEOPLE FOR THEIR NEEDS etc.
- QUARANTINE fourteen DAYS IF Y'all ARE TRAVELLING FROM Abroad OR Take chances Surface area
- QUARANTINE YOURSELF IF Yous Have Any FEVER, COUGH OR SHORTNESS OF BREATH etc.
- FIRST Telephone call YOUR Dr. OR EMERGENCY MEDICAL LINE IF YOU Take SYMPTOMS DO NOT GO TO MEDICAL FACILITIES BY YOUSELF Allow THEM Give YOU THE GUIDELINES AND PICK YOU Upwards
Incident Response Program
An incident response program is a systematic approach taken by an arrangement to assist It Security teams to gear up, observe, comprise, reply and recover from security incidents. The goal of Incident Response Program is to detect and react to security incidents, make up one's mind their scope and risks, respond appropriately, communicate results and risks to all stakeholders. Also reduce costs, recovery fourth dimension and likelihood of the incident from reoccurring.
This is similar to local health authorities and medical facilities produce their incident handling processes based on the guidelines and plans given by governments, ministry of health, CDCs etc.
Incident Handling Guideline : General guidelines and procedures to IT Security teams for dealing with security incidents. In that location are four fundamental components of a security incident handling guideline:

- Grooming : Establishing and grooming an incident response team, acquiring necessary tools, resources and applying set of controls. (Establishing and training Medical teams, testing kits, restriction on public events, facilities etc.)
- Detection and Analysis : Identifying and investigating suspicious action to confirm a security incident, prioritizing the response based on impact and coordinating notification of the incident (testing, analysis and prioritizing patients, investigating and tracking people those patients contacted with and etc.)
- Containment, Eradication and Recovery : Isolating affected systems to prevent escalation, limit touch, finding root cause of the incident, removing malware, affected systems and bad actors from the environment. Restoring systems and data when a threat no longer remains. (Isolating people or areas that are affected by Coronavirus, treatment at hospitals, etc.)
- Post Incident Action : lessons learned assay, its root cause and response, report opportunities to amend the incident response programme and time to come response efforts (published journals and cases that are shared between medical professionals and countries)
Finish user security awareness
The finish-user is the weakest link in the security chain and it is estimated that more than ninety% of security incidents and breaches involve some kind of human error. We are the weakest link in this pandemic and virus spread from people to people. We should exist following guidelines for coronavirus from wellness authorities.
Digital hygiene
Like terminate-user grooming, digital hygiene is a fundamental principle of information security. Similar with personal hygiene, information technology is almost establishing simple routines to minimize the risks from cyber threats. Digital hygiene practices give users another layer of protection, reducing the risk that a vulnerable node volition be affected and compromise other nodes or networks. Personal and facility hygiene practices give usa another layer of protection, reducing the take a chance that a vulnerable one volition be affected and compromise others.
Isolation
Containment is important before an incident overwhelms resources or increases damage. Most incidents require containment, so that is an important consideration early on in the class of handling each incident. Containment provides fourth dimension for developing a tailored remediation strategy. In lodge to slowdown virus spread and limit amercement we must adhere social isolation and stay home.

Source: https://github.com/ealtili/HowToRespondVirusSpread/blob/master/README.md
0 Response to "The Art of Computer Virus Research and Defense Pdf Github"
Post a Comment